Attack Surface Monitoring (ASM)
Attack Surface Monitoring (ASM) is the continuous process of identifying, assessing, and monitoring all the possible entry points (attack surfaces) that an attacker could exploit in an organization’s IT environment—both known and unknown.
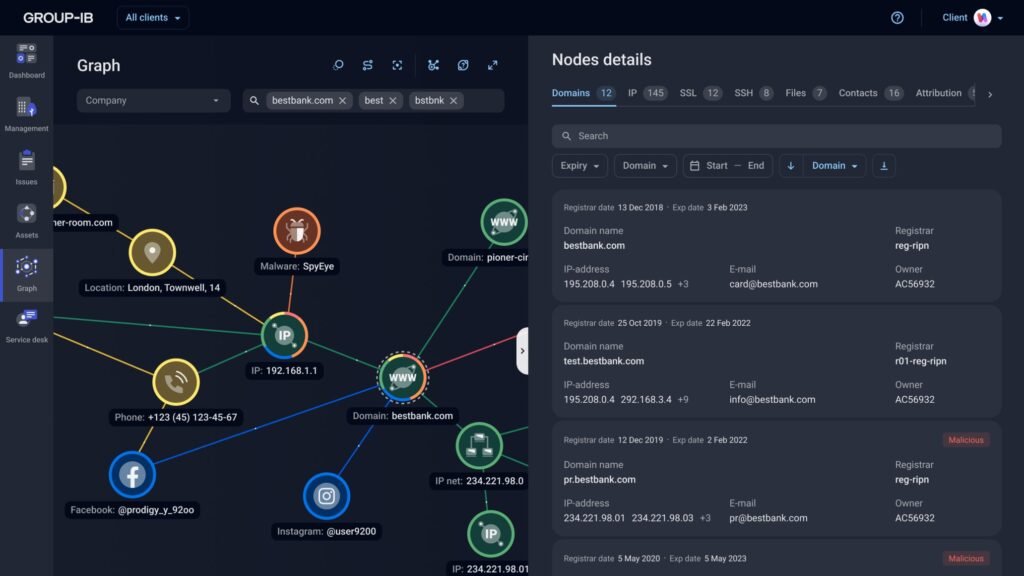
Why ASM is Important
- Organizations often don’t realize how many assets (domains, IPs, cloud apps) are exposed.
- Shadow IT, misconfigurations, and third-party tools expand the attack surface.
- ASM helps reduce risk by identifying and fixing vulnerabilities before attackers find them.
Benefits
- Provides visibility into your true external attack surface.
- Reduces risk by identifying and securing exposed assets.
- Helps prevent breaches by closing open doors before attackers exploit them.
- Supports vulnerability management and incident response.
- Enhances compliance and audit readiness.
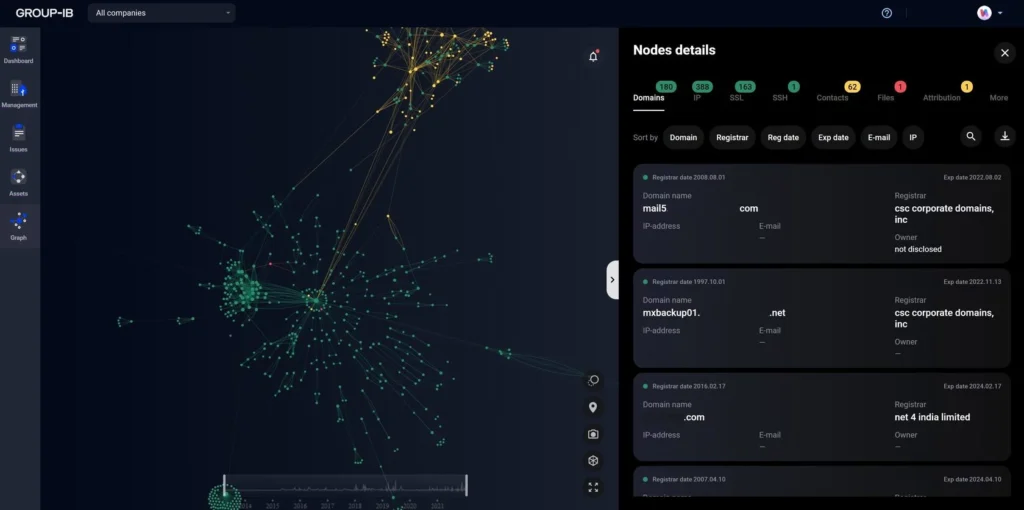
Why Choose This?
With cyber threats evolving daily, proactive attack surface monitoring helps organizations stay ahead of risks, prevent breaches, and maintain a strong security posture.
Our Technology Partner


Discover Caudate Technologies ASM – Proactive Protection, Seamless Security
Let’s start a conversation!
By submitting the form, you are agreeing to our privacy policy.
