Network Security
Take control of your network.
Protect users, devices, and data with a modern NAC solution built for hybrid and remote work
Network Access Control (NAC)
Secure your network by managing who and what connects to it.
Our Network Access Control (NAC) offers advanced, agentless, and flexible network security solutions that extend beyond traditional NAC. These solutions provide comprehensive, resilient, and compliant access control for diverse networks, including IoT/OT environments.
Next-Gen NAC and Network Security
Network Security solutions leverage synergies between network access control, security, and Zero Trust to create a holistic, compliant, and data-centric framework for the business. This approach reduces attack surfaces and aligns with cybersecurity best practices, including highly-regulated industries.
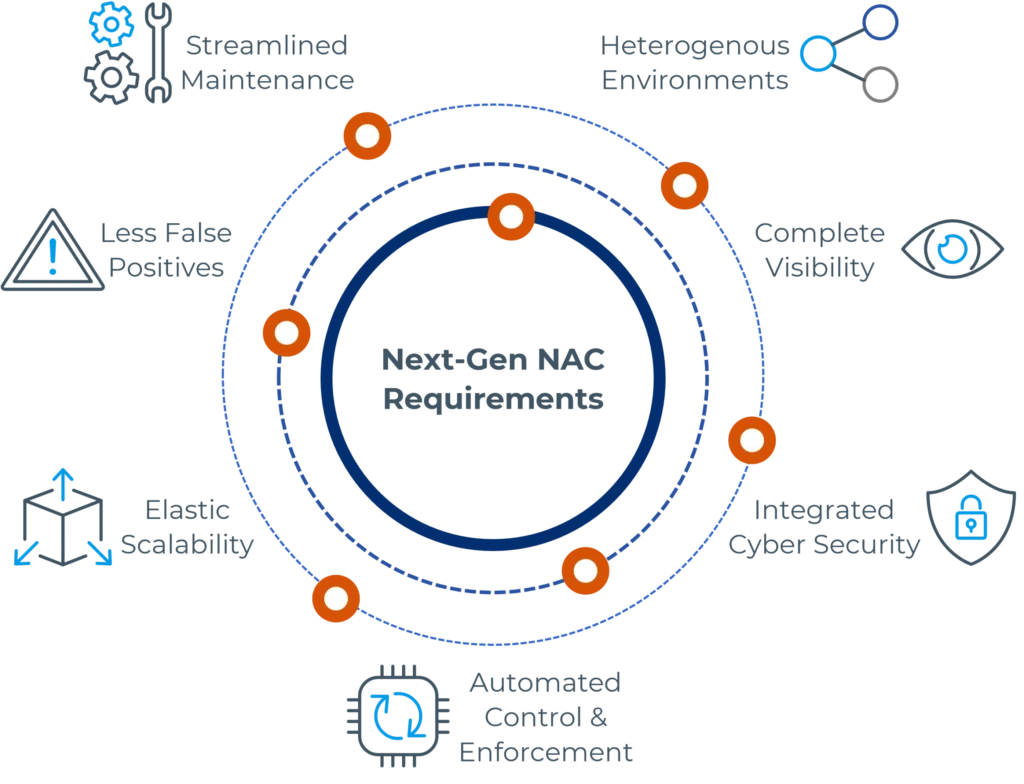
Our next-gen network access control offers a comprehensive, flexible, and non-disruptive approach that provides essential capabilities for enterprises to maintain robust security postures and implement Zero Trust principles effectively.
Our next-gen network access control offers a comprehensive, flexible, and non-disruptive approach that provides essential capabilities for enterprises to maintain robust security postures and implement Zero Trust principles effectively.

Why is NAC Important?
Zero Trust Implementation
Ensures “never trust, always verify” by validating every device and user before granting access.
BYOD Security
Manages risks from employee-owned devices by enforcing security checks before allowing network access.
Regulatory Compliance
Supports compliance with standards like HIPAA, PCI-DSS, and ISO 27001 by tracking and auditing network connections.
Threat Containment
Isolates or blocks suspicious devices in real time to prevent threats from spreading across the network.
How Does NAC Work?
Discovery
Detects all devices attempting to access the network.
Policy Enforcement
Grants or denies access based on rules (e.g., antivirus status, OS version, role).
Authentication
Verifies user credentials and device identity.
Monitoring & Response
Continuously scans network activity and can quarantine or disconnect non-compliant devices automatically.
Our Technology Partner



See Caudate Technologies' DLP in Action – Protecting Your Data, Preventing Leaks
Let’s start a conversation!
By submitting the form, you are agreeing to our privacy policy.
